Confidential Messaging – send me a CM
Everywhere I turn as I set up my practice there’s software that needs writing. Maybe that’s because legal tech is mostly designed for lawyers, not by them. I can’t believe those “contact me” or “send me an email” boxes on attorney websites. They scream malpractice.
I had some fun with CM this week. Confidential Messaging. Like Instant Messaging except a) it isn’t instant, and b) it is confidential.
And I mean “really confidential” – as in, “if I weren’t a lawyer building this for attorney/client privileged conversations, I’d probably be on a no-fly list by now”
The Big Green Button
Here’s a screenshot from my “lawyer” website.
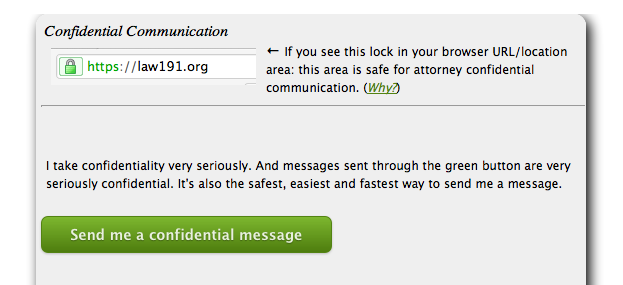
The green button hides some straightforward (but interesting) software issues. And exposes my “Evernote was hacked last week” paranoia.
I’ve written the Confidential Messaging/CM software so that it could be used by any lawyer. For now, it’s just for me and does only what I want. It means that someone can come to my site and send me a message without having to trust the internet. Without compromising. Sure they can phone me – and share their secrets that way, but most of us find it difficult to tell our story out loud to a trusted friend, let alone a complete stranger. It’s much easier to write. And the alternatives? email? bad idea. fax? used to be ok till everyone started using e-faxes. Do you know the route your confidential fax takes on its way to someone else’s virtual fax machine? A sealed letter? great if you can wait. Or if you’re in prison – in which case you aren’t reading this blog. Or if you are, you shouldn’t be and probably need a lawyer. Call me.
This is the age of instant gratification. I want someone to be able to contact me instantly (despite my comment above) and be able to trust that no-one but me can read what they write.
I’m not particularly interested – yet – in two-way communication. This is “send a confidential message down the rabbit hole” – I can take steps to secure the confidentiality of a message that is sent to me – but if I send confidential stuff back, I’m putting the client’s secrets at risk. A client will send a secret to me. She doesn’t need me to send a copy back. And if she wants to talk about it, fine. We’ll talk about it.
Encryption with a sell-by date.
One-way traffic makes it easy (in principle). And it is very easy (in principle). I chose a slightly modified version of the cryptico javascript library. Initially I was tempted with the Stanford Javascript Crypto Library – and its use of elliptic curves for public key encryption. Now I know that curve25519 is supposed to be patent free. But I also know that Certicom are litigious and hold patents that aren’t due to expire for a couple of years. The RSA patents are done. And a 3072 bit key “should” be safe until the year 2030 according to Wikipedia (in whom we trust). It’s a shame, because elliptic curve key pairs would allow me to boast that the system conforms with NSA Suite B.
So that’s the first step. Creating a public/private key pair for the attorney.
Second step is that I want to keep all this “out there” on a hosted site. And I don’t want a private key anywhere it might be hacked, whether it’s on a server in the cloud, or on my laptop. And it has to be accessible or I’ll never read the messages and they will be even less than instant.
I generate my public/private 3072 bit RSA key pair in my browser, using cryptico. And then I encode my private key using 256 bit AES. My public key and my encrypted private key then go to my server. All done over https.
Indonesian Code Talkers
So what’s behind the green button in the screenshot? A nice HTML5 editor (wysihtml5) for the visitor to use to compose her message, and another big green button marked “encrypt.” This encrypts everything using my public key – the message, and the visitor’s details. That block of websafe base64 is then posted to my server.
Actually, I show the visitor the encrypted output before letting her decide to send it to me. The extra step gives her an opportunity to change her mind, and gives me the chance to show off and display the encrypted output onscreen. Curiously, Chrome seems to think that the 3072 bit encrypted base64 message is in indonesian, and offers to translate it for me.
I have a small JSON serialized message “box” on the server. Maybe someone could decode it and find out how many messages I have. But that’s all. Who they are from is encrypted. I upload it and my encrypted private key, type my passphrase in my browser, and read my messages.
Flaws In The Ointment
People often decry using javascript in a browser for encryption. Mostly that’s because it sounds like a good way of avoiding buying a $60 certificate so you can run your site using HTTPS. And that is a bad idea. Person in the middle attacks may be politically correct, but they aren’t very pleasant. But I did spend $60, so that’s not a problem.
Another more serious reason is that even if you are using HTTPS, then your server itself could be an entry point for the person in the middle. And since you are serving the page and the code behind it from your server, no user can tell whether they are using your software or a version hacked by the secret service who have taken over your site and are running a sting operation from it. This is known as the “secret service person in the middle of your server” attack.
How is that different from the “Anonymous person in the middle of my server” attack? I’m glad you asked.
Mostly it’s different because Anonymous (unlike the Men in Black) have to come in through a back door, often called “an exploit.” You can take care not to be vulnerable to some of these exploits. You sanitize input data to stop code injection and XSS attacks. You use POST/XMLHttpRequest and avoid request forgeries. You prevent SQL injection by not using SQL 😉 You protect your file system by constructing paths on the server. And you avoid session issues by using HTML5 effectively in the browser and going back to stateless context-free interactions between the browser and the server.
Also, with Anonymous, you can ssh in to your site every five minutes and check the integrity of your files and maybe catch these “exploits” – or call your ISP and ask them to take your site down – a strategy that numerous governments and corporations have had to do in recent years.
With the “secret service person in the middle of your server” attack, you are likely to be in the brig of an unnamed naval base for the duration of the operation, or have your hands shackled behind your back, making it difficult to use ssh to connect to your web server.
But the “secret service person in the middle” can only set up a sting. They can’t read messages that were sent before the sting started. At least until 2030 if Jimmy Wales is to be believed. And hopefully the statute of limitations for whatever you tell me will have lapsed by then.
Live Free And Die
That leaves a third form of attack. The “tell me your password or I’ll do bad things” attack. That’s different from the person in the middle who takes control. A good attorney, like a good journalist will (of course) take her secret to the grave.
So, my design has the “secret service person in the middle of my server” flaw. Which won’t keep me awake all night worrying about malpractice suits for negligent use of technology. Attorney/client confidences are mostly privileged. Fruit of the poisoned tree, if I remember question 6 of the July 2012 bar exam correctly. If you are an attorney in the JAG corps, or your client risks walking into a passing drone, then maybe you want to avoid my green button.
Afterword
There is a serious side to this blog post. The best security is public. The best security design is a public design. I make light of the flaws and weaknesses, but they are real. And glib statements about security are usually followed by humble retractions. I’d rather understand the flaws than make rash claims. And then I’d like to fix them. So I tell the story of my CM design here. If you decide to hack it, please do so, and please, please explain where the weaknesses are. I won’t sue. Honest. You can trust me. I’m a lawya.


Leave a Reply